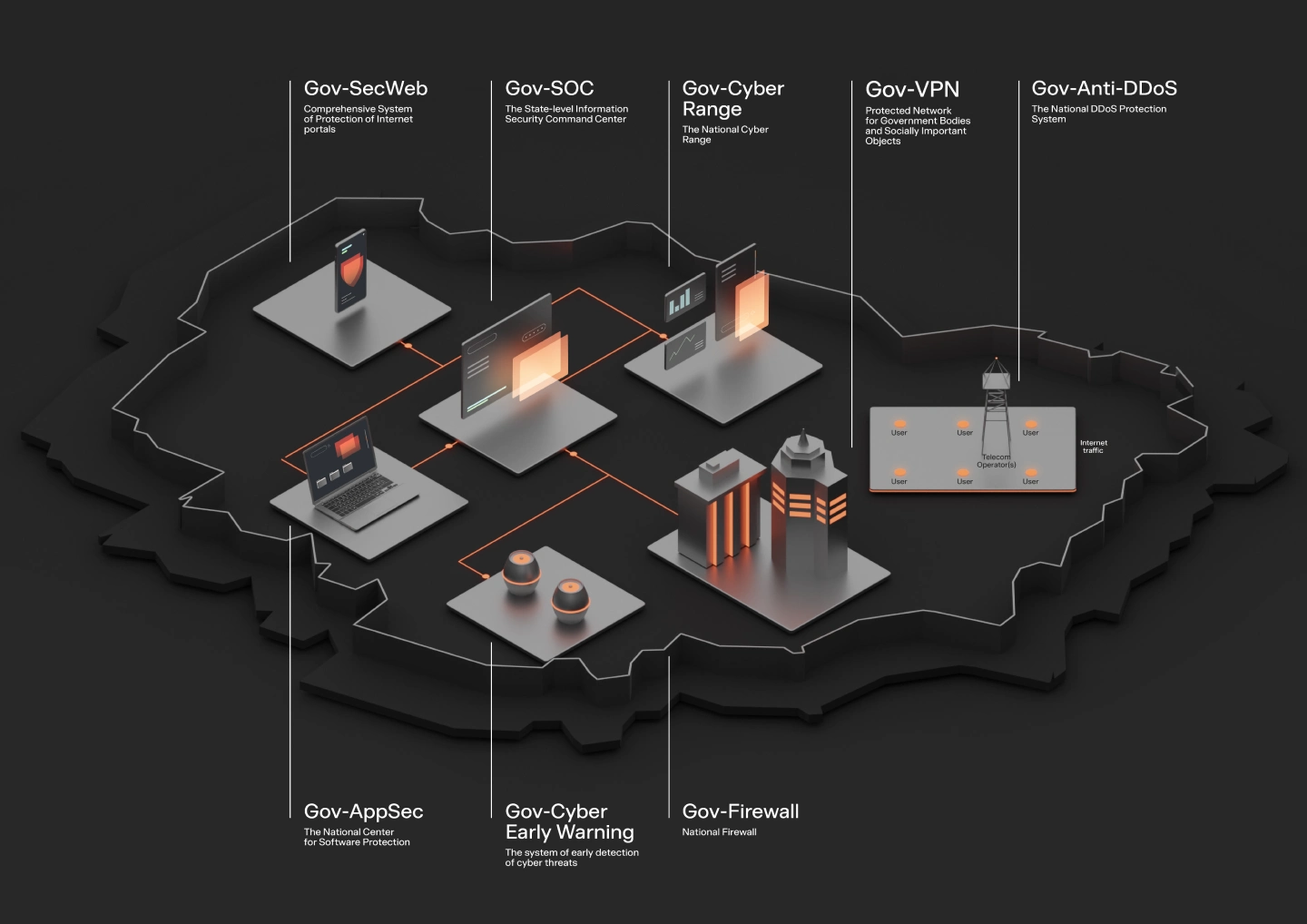
Solar Group is an
architect of complex cybersecurity
Key areas of activity - IS outsourcing, development of own products, training of IS specialists, analytics and research of cyber incidents.

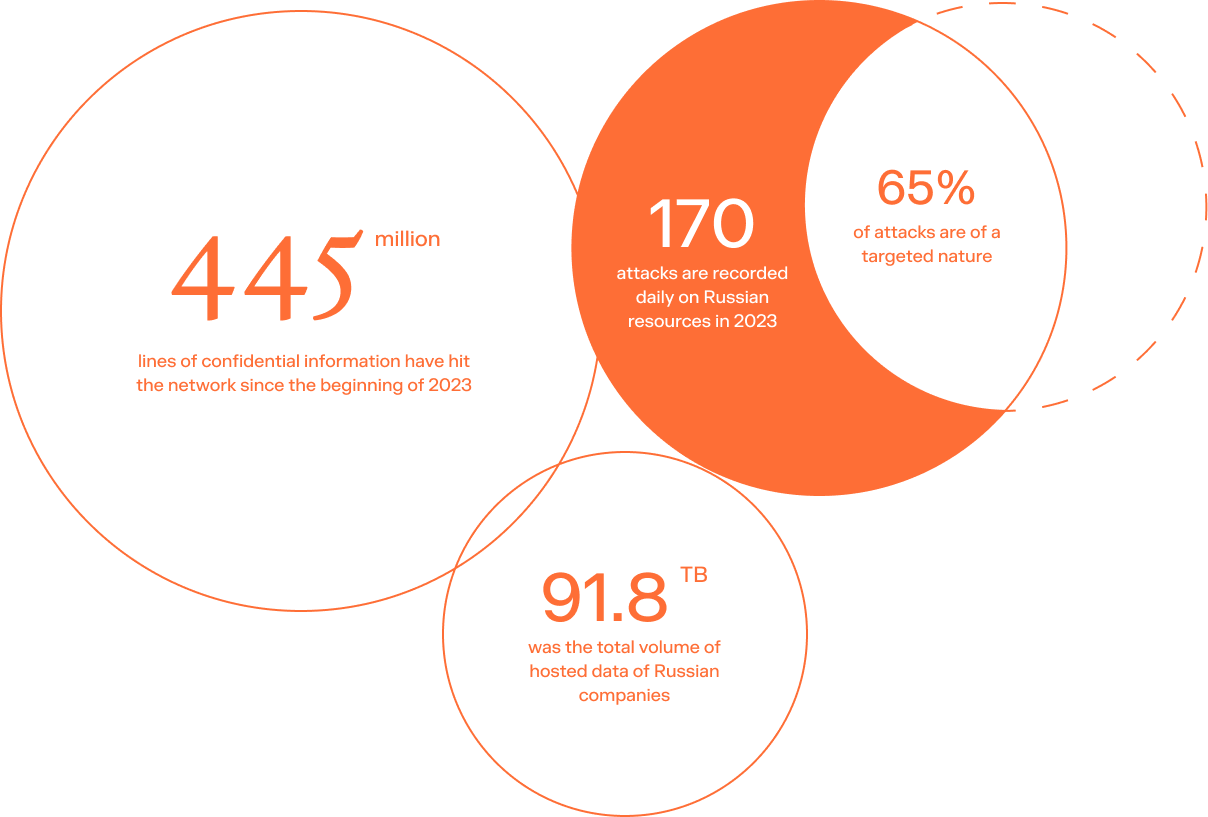
850
significant companies in Russia are protected by Solar over 9 years